Mac address was stolen by hacker/cracker from wifi/wireless along with other information. I am in the process of installing and connecting through another connection for my office. The wireless feature has been removed from the modem and will be disabled from the get go. How to crack wifi Password by Fern WIFI cracker Tool Fern WiFi Cracker is a wireless security auditing and attacking tool written in Python, this tool can crack WPA/WPA2/WEP networks and also can perform MITM attacks Features of Fern WiFi Cracker Tool. WEP cracking; WPA/WPA2 Cracking Dictionary Based Attack, WPS based attack; Automatic Access.

Today i am going to Show you How to track any MAC-address Geographical Location using kali linux. This trick is helful in finding lost devices. Open Applications kali linux wireless Tools 802.11 Wireless Tools Fern-wifi-crecker. KisMAC is a wireless stumbler and cracker that can perform a number of WiFi related tasks directly from your Mac’s operating system. WEP keys are compromised by a process known as WEP injection where data packets are used to determine the password. Access Point MAC Address Geo Location Tracking; Internal MITM Engine; Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP) Update Support; Fern Wifi Cracker Installation. Installation Debian Package supported systems: root@host:# dpkg -i Fern-Wifi-Cracker1.6all.deb. The source code for the program can be fetched using the following command on terminal.
| '' |
| Fern-Wifi-Cracker 2.0 Not working with Ralink Chipsets (tested on AWUS036NH ) |
| What steps will reproduce the problem? |
| 1.start fern-wifi |
| 2.select interface |
| What is the expected output? What do you see instead? |
| expected output: 'Monitor mode enabled on wlan0mon' |
| instead: stuck in set_monitor_thread() |
| What version of the product are you using? On what operating system? |
| Linux Mint 64: |
| Linux xxxxxxxx 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:30:00 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux |
| Please provide any additional information below. |
| the reason: you only search for monitors with *mon pattern |
| realtek chipsets and recent airmon-ng version use a new pattern: wlandmon |
| here is a bugfix, i use for my version: |
| '' |
| defset_monitor_thread(self,monitor_card,mac_setting_exists,last_settings): |
| #print 'starting new thread' |
| status=str(commands.getoutput('airmon-ng start %s'%(monitor_card))) |
| #print 'nStatus of airmon-ng start', monitor_card, ':', status,'n' |
| if ('monitor mode enabled'instatus) or ('monitor mode vif enabled'instatus): #fix for ralink if |
| monitor_interface_process=str(commands.getoutput('airmon-ng')) |
| #print 'monitor_interface_process:', monitor_interface_process, 'n' |
| if ('monitor mode enabled'instatus): |
| regex=re.compile('mond',re.IGNORECASE) |
| elif ('monitor mode vif enabled'instatus): |
| regex=re.compile('wlandmon',re.IGNORECASE) #changed from mond to wlandmon |
| interfaces=regex.findall(monitor_interface_process) |
| print'available interfaces:', interfaces |
| if(interfaces): |
| self.monitor_interface=interfaces[0] |
| else: |
| self.monitor_interface=monitor_card |
| print'setting self.monitor_interface to', self.monitor_interface |
| variables.monitor_interface=self.monitor_interface |
| self.interface_combo.setEnabled(False) |
| variables.wps_functions.monitor_interface=self.monitor_interface |
| self.emit(QtCore.SIGNAL('monitor mode enabled')) |
| # Create Fake Mac Address and index for use |
| mon_down=commands.getstatusoutput('ifconfig %s down'%(self.monitor_interface)) |
| ifmac_setting_exists: |
| variables.exec_command('macchanger -m %s %s'%(last_settings,self.monitor_interface)) |
| else: |
| variables.exec_command('macchanger -A %s'%(self.monitor_interface)) |
| mon_up=commands.getstatusoutput('ifconfig %s up'%(self.monitor_interface)) |
| foriterateinos.listdir('/sys/class/net'): |
| ifstr(iterate) str(self.monitor_interface): |
| os.chmod('/sys/class/net/'+self.monitor_interface+'/address',0777) |
| variables.monitor_mac_address=reader('/sys/class/net/'+self.monitor_interface+'/address').strip() |
| variables.wps_functions.monitor_mac_address=variables.monitor_mac_address |
| else: |
| print'problem occured while setting up the monitor mode of selected', monitor_card |
commented Jan 4, 2015
now intergrated in Fern-Wifi-Cracker 2.1 ( https://code.google.com/p/fern-wifi-cracker/issues/detail?id=97 ) |
commented Jan 21, 2015
Hello, I use Kali Linux in VMware Fusion (Mac OS X). When i choose the wlan0 (AWUSO36NH) on fern-wifi, a problem appears ... I'm trying to attack and WPA access. So i think Fern-Wifi Cracker doesn't work well with AWUS036NH. Sorry for my poor english. |
Some of the codes might not work in your Smart Phones …..

******* Use at your own risk!!!!!
——————————————————————————————————————–
*#*#4636#*#* Information about phone and batteries
*#*#7780#*#* Reset data like before
*2767*3855# Format Phone
*#*#197328640#*#* Launch service mode
*#*#232339#*#* Test WiFi
*#*#197328640#*#* Log mode service
*#*#1472365#*#* GPS test
*#*#1575#*#* Other GPS test
*#*#232331#*#* Bluetooth test
*#*#232337#*# Displays Bluetooth address
*#*#0*#*#* LCD test
*#*#0673#*#* Melody test
*#*#0842#*#* Device tests
*#*#2663#*#* Touchscreen version
*#*#2664#*#* Touchscreen test
*#*#0588#*# * Proximity sensor test
*#*#3264#*#* RAM version
*2767*3855# Factory reset
General Codes:
*#06# –Display’s IMEI number.
*2767*3855# –Format your device to factory state (will delete everything on phone).
*#*#4636#*#* – Display’s Phone information, usage statistics and battery.
*#*#273282*255*663282*#*#* –Immediately backup of all media files.
*#*#197328640#*#* –Enable test mode for service.
*#*#1111#*#* –Displays FTA software version.
*#*#1234#*#* –Shows PDA and firmware version.
*#*#232339#*#* – Wireless LAN tests.
*#*#0842#*#* –Backlight/vibration test.
*#12580*369# – Displays Software and hardware info.
*#*#2664#*#* – Testing the touchscreen.
*#9900# – System dump mode.
*#9090# – Diagnostic configuration.
*#*#34971539#*#* –Displays Detailed camera information.
*#872564# – USB logging control.
*#301279# – HSDPA/HSUPA Control Menu.
*#7465625# –Display phone’s lock status.
*#0*# – Enter the service menu /LCD Test Mode.
*#*#7780#*#* – Reset the /data partition to factory state.
Basic Codes:
*#*#7780#*#* – Factory restore setting.Removes Google account setting & System and application data and settings.
*2767*3855# – Factory format, and will remove all files and settings including the internal memory storage. It will also re-install the firmware.
*#*#4636#*#* – Shows information about your phone and battery.
*#*#273283*255*663282*#*#* – Opens a File copy screen where you can backup your media files e.g. Images, Sound, Video and Voice memo.
*#*#197328640#*#* – Enter into Service mode.
*#*#7594#*#* – Enables your “End call / Power” button into direct power off button without asking for selecting any option(silent mode, aero plane and power-off).
*#*#8255#*#* – Launches G Talk Service Monitor.
*#*#34971539#*#* – Camera information. Please avoid update camera firmware option.
Fern Wifi Cracker Wordlist
W-LAN, GPS and Bluetooth Test Codes:

*#*#232339#*#* OR *#*#526#*#* OR *#*#528#*#* – W-LAN test (Use “Menu” button to start various tests).
*#*#232338#*#* – Shows WiFi MAC address.
*#*#1472365#*#* – GPS test.
*#*#1575#*#* – Another GPS test.
*#*#232331#*#* – Bluetooth test.
*#*#232337#*# – Shows Bluetooth device address.
Fern Wifi Cracker Tutorial
Codes to launch various Factory Tests:
*#*#0842#*#* – Device test (Vibration test and BackLight test).
*#*#0588#*#* – Proximity sensor test.
*#*#0*#*#* – LCD test.
*#*#2664#*#* – Touch screen test.
*#*#2663#*#* – Touch screen version.
*#*#0283#*#* – Packet Loopback.
*#*#0673#*#* – Melody test.
*#*#3264#*#* – RAM version.

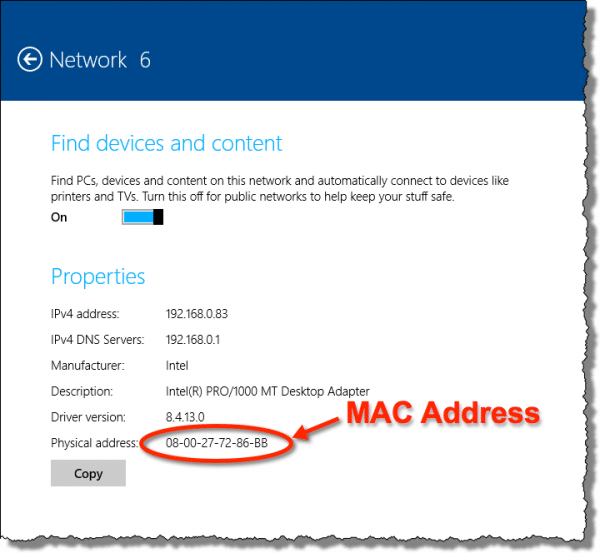
Code for firmware version information:
Fern Wifi Cracker Mac Address Free
*#*#1111#*#* – FTA SW Version.
*#*#2222#*#* – FTA HW Version.
*#*#44336#*#* – PDA, Phone, CSC, Build Time, Changelist number.
*#*#4986*2650468#*#* – PDA, Phone, H/W, RFCallDate.
*#*#1234#*#* – PDA and Phone